The neural system of most of the enterprises is the network. With the emergence of social networking, video streaming, peer-to-peer technology, cloud computing and SaaS, it's safe to say that modern enterprises are only as good as their networks especially in terms of the bandwidth and security they provide. Be it banks securing their data against thefts or business organizations securing their network against security threats and attacks, the lurking threat of getting breached, compromised and damaged by an unknown zero-day intruder is always relevant. Moreover, continuous evolution of intrusion techniques has made the task of ensuring network security increasingly difficult in spite of becoming all the more critical.
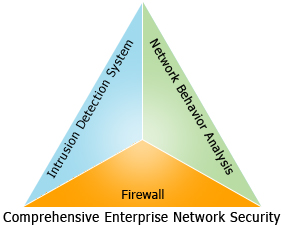
Predominantly, the security systems are classified into three types. They are (i) Firewall Systems, (ii) Intrusion Detection/Prevention (IDS/IPS) Systems and (iii) Network Behavior Analysis (NBA) Systems also known as Network Behavior Anomaly Detection (NBAD) Systems. While all three of them have their own unique strengths and weaknesses, they complement each other to form a holistic network security strategy. However, the first two are widely prevalent and perceived as essential components, the third is not so. This leaves the network vulnerable to several zero-day attacks, unknown worms, internal threats, etc., as well as letting them lag behind in terms of overall traffic visibility, access policy decisions, security posture assessment and a reasonably sure confirmation of network security.
Comprehensive Enterprise Network Security:
 Unified bandwidth monitoring and zero-day security analytics
Bandwidth monitoring & traffic analysis and network security analytics & behavior anomaly detection are interdependent and complementary by nature. NetFlow Analyzer, coupled with ASAM, unifies these complementary solutions to provide a holistic and reliable decision support system in a single user-friendly interface. While NetFlow Analyzer gives you an in-depth visibility in to your network traffic and bandwidth utilization, ASAM offers continuous network security monitoring and anomaly detection capabilities.
Unified Traffic Analytics:
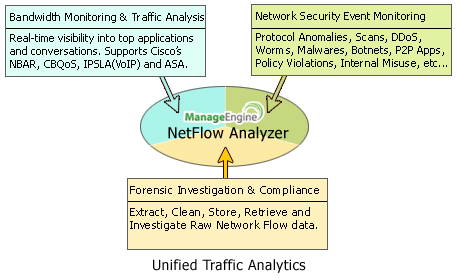 Advanced Security Analytics Module (ASAM)
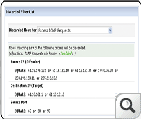
Advanced Security Analytics Module is a network flow based security analytics and anomaly detection tool that helps in detecting zero-day network intrusions, using the state-of-the-art Continuous Stream Mining Engine™technology, and classifying the intrusions to tackle network security threats in real time. ASAM offers actionable intelligence to detect a broad spectrum of external and internal security threats as well as continuous overall assessment of network security (Network Security screenshots).
ASAM Technological Significance:
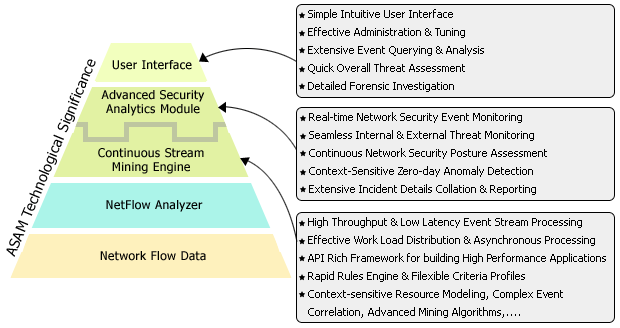
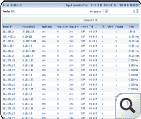
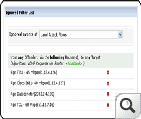
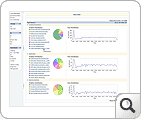
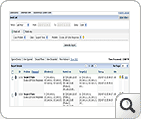
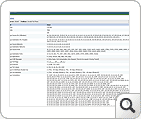
The Security Snapshot of ASAM displays a list of grouped threats/anomalies as problems and further, the problems are categorized in to three major problem classes (Bad Src-Dst, DDoS, Suspect Flows). The set of classes used for classifying problems with a brief description is given here (Problem Taxonomy). The pie charts and line graphs help the user grasp the overall network "security posture" in one glance. On further drill-down it displays a list of individual events/anomalies, of a specific problem, with detailed information collation for closer investigation by the operator.
ASAM, offered as a simple add-on module of NetFlow Analyzer, leverages the underlying platform's agentless centralized data collection and forensic analysis capabilities, to offer greater value. NetFlow Analyzer is a robust, scalable and a proven platform offering bandwidth monitoring and unified traffic analytics.
Benefits of ASAM:
Technical Capabilities:
Features:
|
Menggunakan kemampuan Advanced Security Analytics Module (ASAM) di Netflow Analyzer untuk analisa sekuriti jaringan
Dalam produk Netflow Analyzer, ada salah satu modul ASAM yang digunakan untuk melakukan analisa sekuriti jaringan.
You may like these posts
Popular Posts

Dunia Aplikasi OpenSource
March 04, 2013

FTTH jaringan akses Fiber Optik dan teknologi G-PON
October 28, 2017
Ruang kerja terpadu = Unified Workspace dengan Awingu
October 27, 2017
Latest Video
Our Videos
3/Videos/post-list
Menu Footer Widget
Created By SoraTemplates | Distributed By Blogger Themes