Simple Secrets of Successful Knowledge Management
Simple Secrets of Successful Knowledge Management A sound knowledge base eliminates the need to rediscover or reformulate knowledge. March 6, 2017 LeAnn Smiles KEYWORDS service-oriented architecture Reprints 13 36 No Comments Knowledge that doesn’t serve is knowledge wasted. And for knowledge gained from experience and research to be useful, IT enterprises need to organize, manage, and offer it in the best way possible. Fortunately, the best way isn’t a Herculean task when you employ simple tricks to build a profo…
Declining Enterprise Data Backup Market Challenges Vendors
Declining Enterprise Data Backup Market Challenges Vendors Posted September 22, 2017 By Pedro Hernandez Send Email » More Articles » The worldwide market for purpose-built backup appliances took a beating during the second quarter (Q2) of 2017. Revenue slipped 16.2 percent on an annual basis, dropping to $728.5 million compared to $868.9 in Q2 2016. The open systems segment generated sales of $657.9 million. Mainframe backup revenue dropped 15.4 percent. In total, vendors shipped 858PB of backup storage capacity in Q2, a decline …
AFFRAID OF COMMITMENT
AFFRAID OF COMMITMENT ( Ketakutan untuk berkomitmen ) Namanya Tia, Head of Marketing di sebuah perusahaan Korea di Jakarta. Malam itu dia ngajak dinner karena ingin menceritakan konflik yang dihadapinya dan ingin minta masukan saya. Malam itu kami makan di restauran Jepang di daerah Sudirman. "Saya mengelola sebuah team dengan sekitar 30 an karyawan.Yang langsung repport ke saya ada 6 orang. Jadi secara terathr saya rapat dengan ke 6 orang anak buah saya itu." Tia memulai ceritanya dan meneguk Jus Tomat di depannya. "Masalahnya…
Amankan akses Internet untuk siswa Anda dengan NetSupport DNA
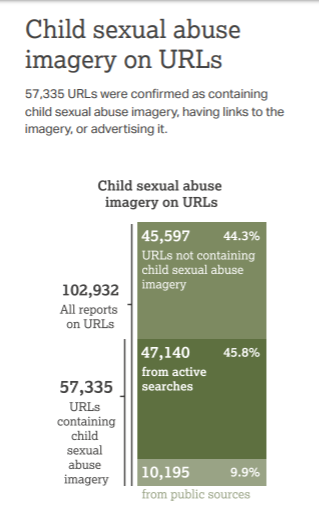
Salah satu data dari Internet Watch Foundation (iwf.org.uk), banyak terjadi kasus pelecehan seksual terhadap anak-anak (child abuse), dimana data menunjukkan masih tingginya kasus terjadinya menggunakan media Internet. Dan cara yang paling banyak adalah dengan menggunakan akses melalui URL dan mengambil gambar (image). Selain itu, juga banyak ditemukan di dalam newsletter. Data diatas juga menunjukkan peningkatan jumlah, terutama untuk gambar anak perempuan. Apabila kita melihat sumber negara, maka data ini yang ditunjukkan. …
Popular Posts




Social Plugin