Welcoming 2011..
Tahun 2010 merupakan tahun yang mengagumkan bagi kami semua di PT.DCMS. Selain karena banyaknya hal yang kami bisa buat sepanjang tahun, kami juga memiliki tim yang solid dan kerjasama internal dan eksternal yang baik. Dan kami sangat bersyukur oleh karena itu semua. Tahun 2011, tantangan baru sudah tampak di depan mata. Selain ada beberapa pekerjaan yang sedang berjalan dan harus segera selesai di Januari 2011. Kami juga berharap akan banyak hal. Kami berharap kami bertambah solid dengan adanya nanti datangnya tim baru yang akan bergab…
LOWONGAN URGENT
Kami membutuhkan : 1. PROGRAMMER VB/VB.NET - Menguasai VB/VB.NET - Mengerti koneksi ke database MySQL - Lebih disukai Fresh Graduate - Female 2. PROGRAMMER PHP/FLASH - Menguasai PHP/ Framework / Flash - Mengerti koneksi ke database MySQL - Lebih disukai Fresh Graduate - Female kirimkan CV ke hrd@dayaciptamandiri.com / fankychristian@gmail.com thanks, Fanky
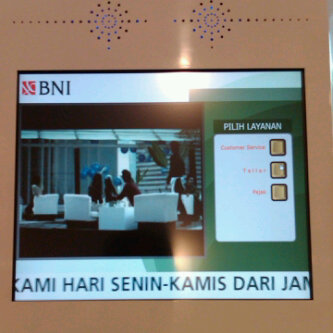
Selamat atas implementasi finosSQM
Selamat kepada BNI yang telah memilih finosSQM sebagai solusi sistem antrian multimedia di kantor cabang. Kami bangga melayani Anda. build-access-manage on www.dayaciptamandiri.com
Sejarah Internet Indonesia
Mencari bahan sejarah Internet Indonesia, bisa diakses di : http://opensource.telkomspeedy.com/wiki/index.php/Sejarah_Internet_Indonesia regards, Fanky Christian
Ensuring an ERP implementation delivers
Now that we've examined how to evaluate your ERP readiness and how to purchase the right system, let's look at the burdens of an ERP implementation and the organization's responsibility in meeting them. At the same time, let's consider how to maximize your organization's ability to capture ERP's potential, boost your ROI and avoid common mistakes. Define the ERP implementation strategy Even with a perfect business survey and total understanding of the enterprise, any organization faces formidable implementation challeng…
Selamat kepada PT. TASPEN (Tbk)
Selamat kepada PT.Taspen (Tbk) yang telah memilih solusi Fusioncharts untuk memaksimalkan visualisasi aplikasi dengan menggunakan XML/HTML5. Fusioncharts merupakan produk unggulan dari Infosoft Global Private Ltd, berbasis di Hongkong dan India. Produk Fusioncharts merupakan salah satu produk terbaik mereka yang banyak digunakan oleh banyak perusahaan, instansi dan website personal untuk memvisualisasikan charts dengan cara yang mudah dan elegan. Kami sebagai sole-reseller untuk Indonesia sangat bangga memiliki produk unggulan ini, yang banyak…
Zoho Targets the Enterprise With New Accounting, Telephony Functionality
Zoho has enhanced its CRM app with new accounting and telephony functionality via integration with QuickBooks and several telephony systems. Zoho CRM for QuickBooks and Zoho PhoneBridge -- which hooks into PBX systems from Asterisk, Avaya, Elastix, and Trixbox -- each take about 20 to 30 minutes to download and configure, Raju Vegesna, Zoho evangelist, told CRM Buyer. Zoho added the functionality in pursuit of its larger goal to expand its reach into related CRM areas, such as order management and call tracking, and embed itself deeply into th…
10 ways to keep hard drives from failing
10 ways to keep hard drives from failing Posted in: 10 things Hardware prices have dropped considerably over the last decade, but it's irresponsible not to care for the hardware installed on machines. This is especially true for hard drives. Hard drives are precious commodities that hold the data employees use to do their jobs, so they should be given the best of care. Inevitably, those drives will die. But you can take steps to prevent a premature hard disk death. Let's examine 10 such steps to care for the health of your drives. Note…
Data center facilities equipment and design stats from Gartner conference
Posted by: Matt Stansberry At this week's Gartner Data Center Conference in Las Vegas, research VP John Phelps asked users a series of questions about their data center facilities technologies. Here are some of the stats: What type of data center fire suppression system do you have? -Water sprinkler only 21% -Water plus clean agent 50% -Clean agent only 21% -Don't know 8% "For those of you with water-only systems, if those sprinklers go off you will be in a world of hurt," Phelps said. "The goal of a sprinkler system is …
Selamat kepada ACSC Banjarmasin
Selamat kepada ACER Service Center di Banjarmasin yang telah mengimplementasikan sistem antrian multimedia finosMQS. Sistem antrian multimedia finosMQS terbukti sangat membantu untuk mengukur kinerja layanan staf dan menentukan langkah terbaik bagi manajemen untuk memberikan layanan terbaik dan terukur dari waktu ke waktu. Produk finosMQS telah dipasarkan sejak tahun 2005 dan ACER merupakan customer yang setia menggunakan produk ini. Kami senang melayani ACER. Kontak kami untuk keperluan sistem antrian multimedia di perusahaan / tempat Anda. F…
5 Higher Ed Tech Trends To Watch in 2011 (Outside Indonesia)
5 Higher Ed Tech Trends To Watch in 2011 Three higher ed tech experts discuss technology trends for the year ahead, citing increased mobile and wireless access and cloud computing among them. But are campuses also in for a little bit of a return to the "basics" in the coming year? * By Bridget McCrea * 12/09/10 Technology that was unimaginable a decade or so ago is commonplace on today's campuses. In 2010 American colleges and universities responded to the ever-advancing IT requirements of their students and faculty with …
Ozeki NG SMS Gateway v3.16 released
for SMS,MMS and Voice calls Check out the new voice call feature... Ozeki NG is known to be a very reliable software when it comes to SMS/MMS messaging. It can handle large load of traffic and it operates seemlesly in the background 24/7. It also integrates very well with the corporate infrastructure as it can send SMS messages directly from a database through various communication channels. With the release of Ozeki NG v3.16, companies will have a new ability to dial telephone numbers automatically and to play in a voice messages after the c…
Navicat for SQL Server
Today we are glad to announce the release of Navicat™ for SQL Server, adding a new member to the Navicat family. To meet the wishes of Navicat customers and the demand of managing Microsoft® SQL Server database through a GUI, Navicat for SQL Server is introduced to the Navicat family in this launch. This new product provides SQL Server users a tool for administering and managing database objects as well as for database migration, data import, export, synchronization, reporting, and more. Major Features in Navicat for SQL Server: # Support of M…
Five+ tips to ensure PCI DSS compliance
On occasion, I help a friend who owns several businesses. His latest venture is required to comply with the Payment Card Industry Data Security Standard (PCI DSS). My friend is computer savvy. So between the two of us, I assumed the network was up to snuff. Then went through a compliance audit. The audit was eye opening. We embarked on a crash course in PCI DSS compliance with the help of a consultant. My friend thought the consultant could help prepare for the mandatory adoption of PCI DSS 2.0 by January 1, 2011. The PCI Security Standards Co…
Selamat kepada SRIWIJAYA EYE CENTER
Selamat kepada Sriwijaya Eye Center, Palembang, yang telah mengimplementasikan sistem antrian finosSQM untuk mendukung operasionalnya. Kami sungguh senang melayani Anda.
Anda kesulitan mencari ujung patchcord cables ?
Seringkali dalam melakukan troubleshooting terkait perkabelan, khususnya cat5e dan cat6 di ruangan data center akan menemukan kesulitan. Hal ini semata karena kurang baiknya dokumentasi yang kita lakukan. Untuk menolong kita menemukan kabel yang tepat, maka Patchsee memberikan solusinya. Dengan mengganti kabel patchcord Anda dengan menggunakan kabel PatchCord PatchSee, maka dengan mudah kita bisa menemukan cable yang kita cari. PatchSee juga memudahkan kita untuk membedakan warna dengan menggunakan tag warna yang ada. Silahkan kontak kami untu…
A New Approach to Business Intelligence: Rapid-fire BI
A New Approach to Business Intelligence: Rapid-fire BI What is this new generation of business intelligence? Whether you've heard it called new BI, self service BI or rapid-fire BI, this whitepaper will help you and your IT team make sense of what it is, how to identify it and how you and your organization can benefit. Business intelligence initiatives continue to top CIO priorities, as executives and managers demand greater visibility into business data much faster. Traditional business intelligence platforms have fallen short of deliveri…
Welcome to the 2010 Open Source Awards : Packt Open Source Awards 2010
The Open Source Awards is a contest that aims to encourage, support, recognize and reward Open Source projects. The winners of the 2010 Open Source Awards are listed below. To identify the excellence among Open Source projects, public votes for the finalists in each category were combined with ratings from a panel of Judges. Winners Open Source CMS Every Content Management System (CMS) that is based on one of the Open Source licenses were eligible to participate in this category. We are pleased to announce that CMS Made Simple has won the Open…
Gartner Identifies Four Converging Trends That Will Change the Face of IT and Business
Analysts Look Back and Forward 20 Years in IT as Gartner Celebrates 20 Years of Symposium/ITxpoSydney, Australia, November 15, 2010 — From social media to intelligent devices to cloud computing, evaluating how these technologies fit into an organization and their impact on the bottom line will become a critical function of the C-level executive, according to Gartner, Inc. In future, the impact of IT on revenue will be directly related to the financial compensation of CIOs. Speaking in the keynote presentati…
Gartner: 5 tips for cutting data center power consumption
Gartner: 5 tips for cutting data center power consumption By Heather Clancy | November 24, 2010, 5:56am PST Summary When market research and advisory firm Gartner decided to remove green data centers from its list of strategic imperatives for 2011, the decision was met with some gnashing of teeth. But, frankly, the decision didn’t really surprise me all that much because energy efficiency, space optimization, infrastructure consolidation, and proper disposal of outdated t…
Check out Untangle 8.0's new Bandwidth Control feature
Check out Untangle 8.0's new Bandwidth Control feature Posted in: In a number of posts previously, I've mentioned the Untangle appliance and its features for providing Internet gateway connectivity. Recently, Untangle 8.0 has been released with the Bandwidth Control feature and, much to my satisfaction, a virtual appliance deployment option for Untangle 8.0 I have used Untangle for a few years for the Internet connectivity and network management for my personal lab. For that network, I provide DNS, DHCP, content filtering, and port and…
HARGA DISCOUNT KHUSUS UNTUK PRODUK FUSIONCHART
Dalam rangka menyambut AKHIR TAHUN 2010, kami memberikan potongan discount khusus untuk pembelian produk FUSIONCHARTS (www.fusioncharts.com) mulai PURCHASE ORDER yang kami terima periode 20 NOVEMBER 2010 - 10 JANUARI 2011 . Silahkan manfaatkan kesempatan ini untuk mendapatkan produk terbaik untuk keperluan visualisasi grafik Anda. Kontak kami: 021-3924716 / 08121057533 Berita terbaru terkait Fusioncharts: FusionCharts, the Industry's leader in Flash Charting, is now ready for iPads and iPhones too.( refer to the link to know more: …
Selamat kepada LEMBAGA SANDI NEGARA
Selamat kepada Lembaga Sandi Negara yang telah mengimplementasi Security Manager Plus, solusi terpadu dari ManageEngine untuk memonitor security jaringan dan server, termasuk patch management yang menjadi kunci kestabilan sistem server. Kami senang melayani Anda.
Selamat kepada LEMBAGA SANDI NEGARA
Selamat kepada Lembaga Sandi Negara yang telah mengimplementasi Security Manager Plus, solusi terpadu dari ManageEngine untuk memonitor security jaringan dan server, termasuk patch management yang menjadi kunci kestabilan sistem server. Kami senang melayani Anda.
Campus Spotlight: Rebuilding IT from the Ground Up
* By Bridget McCrea * 11/04/10 The first thing Bill Seretta did four years ago as American International College's CIO was rip out all of the old cat-3 and coax wires on campus and the equipment that relied on those wires. Then, he replaced the Springfield, MA-based college's entire infrastructure with state-of-the-art wireless options. After all, he said, if you don't have a secure, reliable, high-speed core infrastructure, "you can't do a thing." "This holds true in corporate America, in education, and ever…
NAVICAT - Beta Release Navicat Premium 9.1
We are glad to announce about the release of beta version of Navicat Premium 9.1. ** NOTE ** : If you have bought a license of Navicat 9.0, license keys of Navicat 9.1 will be available to you for FREE on Nov 25. You can login to customer center to retrieve the license key on that day. Major new features: - Support of Microsoft SQL Server (2000 to 2008R2) - Cross data transfer between SQL Server and other database servers - Support of PostgreSQL Server 9.0 - Support of MySQL Server 5.5 - Enhanced user and role management - New Privilege Manage…
TechRepublic: Four types of clients to avoid
Posted in: consulting When you meet with a potential client, you should think about more than just how to meet their project needs; you should also listen and watch for cues that will help you determine if you actually want to work for that client. So how can you spot a problem client? Let's face it - no client is going to tell you upfront that she has a hidden agenda or reveal that every consultant who worked for their company quits mid-project. I look for telltale signs from the four types of problem clients that I've encountered. He…
Selamat kepada BIN
Selamat kepada BIN yang telah memilih implementasi Opmanager dan Netflow Analyzer untuk monitoring dan performansi jaringan nya. Dengan menggunakan OpManager, maka manajemen jaringan dapat dilakukan dengan mudah, dengan implementasi yang mudah dan tampilan yang powerfull. OpManager menjawab kebutuhan monitoring jaringan dengan komprehensif. OpManager yang didukung NetFlow Analyzer memudahkan tampilan monitoring jaringan, server dan perangkat berbasis SNMP lainnya serta memudahkan untuk memonitor penggunaan bandwidth secara intensif dan lengkap…
Selamat kepada Kementrian Perhubungan RI
Selamat kepada Kementrian Perhubungan RI yang telah memilih solusi Fusioncharts untuk melengkapi dan memperindah tampilan aplikasi chart yang ada. Dengan menggunakan FusionCharts, berbagai kemudahan dan visualisasi tampilan charts dapat dilakukan dengan mudah. Hubungi kami untuk keperluan Fusioncharts Anda..
Online content often a victim of plagiarism
Posted in: In past blogs, I've recommended that IT pros increase their (positive) web presence by writing technical articles. This can be done in a personal blog or by writing-for-pay for technical publications. In light of a recent event that has been making the blogosphere rounds, I feel the need to make you guys aware of one the caveats of writing for money on the web: People will steal your stuff. Sometimes they'll steal it without really knowing the concept of plagiarism. They'll run your piece and retain your byline but on th…
Moving from SQL to NoSQL
Moving from SQL to NoSQL Are you thinking on moving your database from a SQL implementation to a NoSQL one ? Sometimes when you decide to move to a different approach lots of doubts pop out of your mind, there are a couple of actions that can make your decision more solid and secure. I'll try to provide some tips that would help you to choose the right NoSQL implementation. When do you need to think about NoSQL ? Often web application start by being implemented on top of MySQL, the one day your application got traction and performance issu…
Popular Posts











Social Plugin